Welcome to Deknatel Seddon & Associates
Risk assessment for financial institutions
Deknatel Seddon & Associates specializes in risks and controls assessments for financial institutions.
We perform a wide range of assessments including IT and cybersecurity, online banking, GLBA 501b Safeguarding Customer Information, BSA/AML, and AI systems assessments.
Read more about our risk assessments...
BANK SECRECY ACT / ANTI MONEY LAUNDERING

Our BSA/AML assessments evaluate risks linked to the Bank’s customers, products and services, and geographical reach. We follow a two-step methodology based on the FFIEC’s BSA/AML Examination Manual.
We cover BSA/AML and OFAC controls using the Core and Expanded Examination Procedures in the Manual.
CYBERSECURITY

In our CYBERSECURITY assessments, we evaluate the inherent risk of cyberattacks on the Bank’s information systems, focusing on the Bank’s Internet-facing technology, products, and services.
We use the FFIEC’s Cybersecurity Assessment Tool (CAT).
We apply the CATs five-level controls maturity model to assess the Bank’s cybersecurity controls.
FAIR LENDING

In our FAIR LENDING assessments, we assess risks by evaluating transaction volumes and inherent risk factors based on the lending activity’s nature and the potential impact of a Fair Lending-related incident.
Our controls assessment is based on the appropriate sections in the Consumer Financial Protection Bureau’s Supervision and Examination Manual (e.g., mortgage origination, loan servicing, commercial lending, and SME/SBA lending).
ONLINE BANKING

In our ONLINE BANKING risk assessments, we analyze customer and transaction volumes and risk ratings for the various online banking services offered by the Bank (e.g,, account lookup, account opening, wire transfers, and ACH payments).
We assess controls over online banking operations, including those related to back-office support, guided by the FFIEC’s booklets on Retail Banking and Wholesale Banking, the FFIEC’s Authentication and Access to Financial Institution Services and Systems, and the California Department of Financial Protection and Innovation’s Reducing the Risks of Corporate Account Takeovers.
INFORMATION TECHNOLOGY
In our INFORMATION TECHNOLOGY assessments, we evaluate IT controls utilizing the FFIEC’s IT Examination Handbook, covering critical areas such as Information Security, Infrastructure, Architecture, and Operations (AIO), Outsourcing, IT Management, Business Continuity, and IT Audit.
This framework is further enhanced by incorporating control assessments from the FFIEC’s Cybersecurity Assessment Tool, alongside best practices outlined in Financial Institution Letters and other state legislation and guidance.

OPEN BANKING

In our OPEN BANKING assessments, we assess risks associated with the transactional capabilities provided by the Bank’s Open Banking APIs and the volume of customers who can access these capabilities, including business customers authorized as Customer Permissioned Entities.
Our control assessment covers securing APIs, authenticating access, and protecting customer information in alignment with these global standards and regulatory expectation and draws on the FFIEC’s Architecture, Infrastructure, and Operations booklet and Authentication and Access to Financial Institution Services and Systems, the Hong Kong Monetary Authority’s Open API Framework, and the Open Web Application Security Project’s (OWASP) API Security Top 10.
AI SYSTEMS

We identify the inherent risk of the Bank’s AI systems using the seven AI risk categories described in NIST’s AI Risk Management Framework.
Our controls surveys are designed for each of the Bank’s “AI actors”, a term used in the Framework (e.g., Model Data Scientist, User Experience / User Interface Designer, AI System Owner / Product Manager).
We assess AI systems controls using surveys based on the Suggested Actions in NIST’s AI RMF Playbook, for the four core components in the Framework: Govern, Map, Measure, and Manage.
We also use controls questions based on the ISO/IEC’s Information Technology – Artificial Intelligence – Management Systems standard (ISO/IEC 42001).
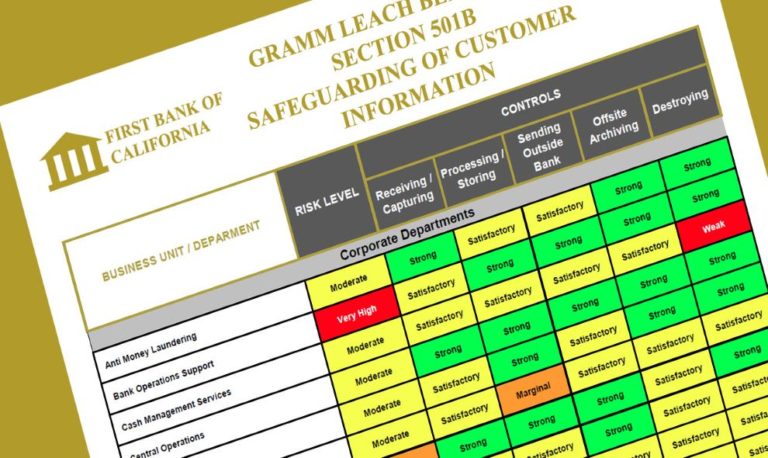
SAFEGUARDING CUSTOMER INFORMATION (GLBA 501B)
Our assessment is based on the FFIEC’s Examination Procedures to Evaluate Compliance with the Guidelines to Safeguard Customer Information.
We create an inventory of the Bank’s electronic and non-electronic customer information systems across all departments, using our pre-populated template.
This inventory is the foundation for our analysis of the Bank’s controls effectiveness in handling customer information—ranging from receipt, processing, storage, transmission, archiving, to destruction.
IDENTITY THEFT RED FLAGS

Our approach to IDENTITY THEFT RED FLAGS assessment starts with creating an inventory of the Bank’s transactions which are subject to the Red Flags and Address Discrepancy Rules, across the different areas of the Bank.
Our assessment of controls focuses on the thirty-six examples of identity theft red flags described in the Rules, plus the examples identified by the Bank’s on-going ID Theft Red Flags Program.
Why Choose Us
Data collection interviews and online surveys are tailored to the management positions and roles and responsibilities in the Bank (e.g. CIO/Director of IT, network manager, BSA Officer, contracts manager) for an efficient and effective way of collecting information.
Our reports follow the structure of regulator guidance, but are customized to the Bank – your products, information systems, vendors, departments, and customer and transaction volumes. Not boilerplate.
Survey responses provide documentation of the Bank’s practices; our reports include descriptions of controls and select control features, and references to the Bank’s policies, standards, and procedures. Examiner- and auditor-ready, these deliverables are also helpful for new employee orientation.
On-line surveys for all our data collection tasks are available Day 1, so managers can start responding at times convenient to them and across multiple sessions. Supporting documentation can be uploaded directly to the relevant survey question, emailed with End-To-End Encryption, or uploaded to a secure Managed File Transfer system.